Ever since the mid-90s, protocols have been used to provide better security and privacy for internet communications. One of the most critical security features for domains is the SSL certificate. In this resource, you’ll learn all about SSL and TLS protocols and how certificates work.
What is SSL?
Secure Sockets Layer (SSL) is a protocol that digitally authenticates ownership of public keys. First developed by Netscape in 1995, SSL provides secure connections between client- and server-side internet communications. The SSL protocol was deprecated with the release of TLS 1.0 (see below).
What is TLS?
TLS stands for Transport Layer Security and is the successor to the SSL protocol. Like SSL, TLS encrypts and authenticates data between servers and web applications. This protocol was developed by the Internet Engineering Task Force (IETF) in 1999. The most current version of TLS is version 1.3, which was released in 2018.
Did you know?: TLS first started development by IETF as SSL 3.1 but was renamed so as not to be associated with Netscape.
SSL vs TLS: What’s the Difference?
According to IETF, there are no major differences between SSL and TLS as they both carry out the same function. That said, TLS is more secure than its predecessor. Servers using the TLS protocol not only require support for a higher level of encryption but must also support the most recent TLS protocols. Old habits die hard, though. While TLS is the preferred protocol, SSL is still used in some cases and TLS is even referred to as SSL—but the term “TLS” is catching on slowly but surely.
In regards to SSL or TLS certificates, there’s really no difference. The terms are used interchangeably regardless of which protocol is being utilized. This is because SSL and TLS certificates follow the X.509 standard format for public keys.
How SSL/TLS Certificates Work
One of the safest and most widely used encryption methods is asymmetrical cryptography, which involves two cryptographic keys: public and private. The public key is used to encrypt data while the private key decrypts it. Picture the public key as a safe with a drop slot. Anyone can add something to the safe, but only the person with the combination can see what’s inside. In this case, the private key holds the combination to the safe. SSL/TLS certificates utilize this type of cryptography to complete what is called a digital handshake.
HTTP vs HTTPS
HTTP and HTTPS are protocols that every website uses. The only difference between them is security. Any site that uses HTTPS also utilizes TLS/SSL to encrypt communication and is, therefore, much more secure than sites running over HTTP. It’s easy for anyone to determine whether a site uses encryption. For example, any URL with HTTPS:// is using TLS/SSL. If it only has HTTP://, the site is not secured by encryption. Another way to spot HTTPS in a website address is by pressing the padlock to the left of the URL. If you click on the lock icon, it will confirm that the site is secure.
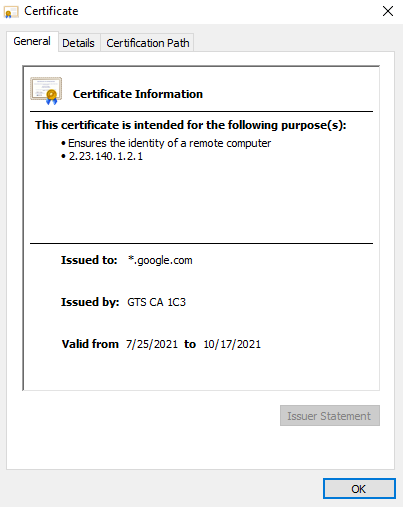
If you click “Certificate,” you’ll also see the certificate authority, including when it was issued and for how long it is valid.
SSL or TLS Handshake
The digital handshake for SSL/TLS represents the events that take place between clients and servers. It entails sending encrypted messages between a client and a server to guarantee the integrity of the data being sent or accessed. Most handshakes follow the pattern below but may deviate if a server uses a different handshake protocol, such as Diffie-Hellman Key Exchange.
- Client greeting (hello)
Client initiates handshake by sending a hello message to an SSL-certified website. - Server greeting (hello)
Server responds with the site’s SSL certificate. - Authentication
Client verifies the certificate - Pre-master secret
The client obtains a public key from the server’s SSL/TLS certificate, and then sends it back as an encrypted string of bytes. - Decryption
Server decrypts the public key (pre-master secret) - Session Keys
The client and server generate random session keys alongside the pre-master secret, which should receive the same results on both sides. - Client and server ready
Client and server both send encrypted “final” messages with session keys. - Secure symmetric encryption achieved
Handshake concludes and communication is continued via session keys.
Types of SSL Certificates
Three types of SSL certificates are available:
- Single Domain
- Wildcard
- Multi-domain
As the name implies, single domain certificates protect one domain and subdomain within its hierarchy. Wildcard SSL certificates function the same as a Single Domain certificate, except it also certifies all first-level subdomains. Multi-domain SSL certificates protect an unlimited amount of domains and subdomains.
SSL Certificate Costs
Prices for certificates range considerably and will also vary depending on the needs of your organization. The type of certificate number of domains and subdomains you have plays a large part in the cost, but other factors such as level of assurance needed, warranty, reissues, key length, and encryption strength should also be taken into consideration.
Free SSL Certificate
Free Certificate Authorities are also an option. While this can save on costs, there may be several limitations to free certificates, so you want to make sure it will meet all your requirements. For instance, many free SSL certificates are trial-based or are only for a limited time before you need to renew. Even if renewal is free, you’ll need to make sure your certificate doesn’t expire. Another caveat is that many free issuers don’t offer business or extended validation. The important thing is that you research all your options before choosing a Certificate Authority for your domain.
Common SSL Certificate Errors
Almost all modern browsers can recognize SSL certificates. But every so often, end users can encounter errors with a domain’s certificate. Knowing what the common errors are can help maintain trust in your website.
- Your connection isn’t private: This happens when a browser can’t verify your domain’s SSL certificate. Because the browser can’t confirm the domain’s identity, it blocks the user from accessing the site.
- Expired certificate: If you don’t renew your domain’s certificate before it expires, users will get an error message alerting them to the fact that your certificate is no longer valid.
- Untrusted Certificate Authority: This error means that the browser was unable to locate the root certificate from a trusted source. It can also happen if a certificate is self-signed and not added to a browser’s trusted store.
Of course, this isn’t an exhaustive list of SSL certificate errors. It is highly advisable that someone on your team is familiar with how certificates work and how to troubleshoot them in case of any unforeseen issues.
SSL Certificate Checker
Luckily, online tools are available to help troubleshoot installation problems and other issues with SSL certificates. Here’s a quick list of a few popular options:
DigiCert SSL Installation Diagnostics Tool
Geocerts SSL Installation Checker
SSL/TLS Certificates Recap
SSL certificates are an important security measure for websites. With an SSL certificate, domains can encrypt web traffic with SSL/TLS protocols for enhanced protection. While SSL is still used by some websites, the preferred and most secure protocol for internet communications is TLS. The bottom line is that certificates not only protect users from suspicious websites, but also help businesses maintain trust in their brand.
End-to-End DNS and Certificate Security with DNS Made Easy
DNS security doesn’t stop at the nameserver level. SSL/TLS certificates are a key part of a complete protection strategy—and DNS Made Easy supports it all. Our platform integrates with leading certificate management tools and provides advanced DNS features that help ensure your domains are secure, responsive, and trusted by users worldwide. From certificate validation to reliable DNS resolution, DNS Made Easy helps keep your infrastructure tight and your online presence protected.
