The domain name system (DNS) is one of those technologies that no one really thinks about—unless it breaks. If you don’t have to think about it, that means your DNS is working like it’s supposed to. But there’s actually a lot more to it than that. Not only does DNS face technical challenges, but it is also vulnerable to certain types of cyber threats. This blog focuses on DNSSEC and how it can help secure the DNS lookup process.
What is DNSSEC?
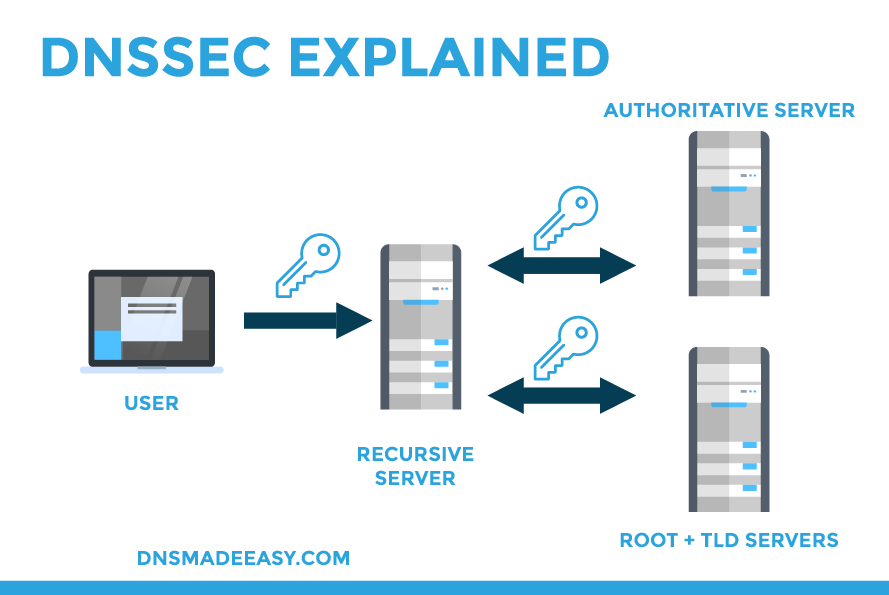
Domain name security extension (DNSSEC) is a set of protocols created by the Internet Engineering Task Force (IEFT). Its purpose is to provide an additional layer of security during the DNS lookup process. When using DNS, queries and their responses are authenticated before an end user is sent to their destination.
How Does DNSSEC Work?
DNSSEC authentication works through cryptographic digital signatures. These signatures are stored on authoritative nameservers alongside a domain’s other DNS records. Each DNS zone has a pair of public and private keys that enable validation: a zone-signing key (ZSK) and a key-signing key (KSK) pair.
Zone-signing Key (ZSK)
The private key in a ZSK key pair creates RRSIG records, which sign the RRSET records in a zone. The public key, stored within a DNSKEY record, verifies the signature. When a DNSSEC resolver queries a DNS record, the responding nameserver returns the RRSIG for that record set. Once the RRSIG is received, the resolver can retrieve the DNSKEY record to authenticate the query.
Key-signing Key (KSK)
A KSK ensures that the ZSK is valid and hasn’t been tampered with, and its private key signs both the ZSK and KSK public keys.
DNS Records Used For DNSSEC
For DNSSEC to work correctly, you’ll need to create the necessary records, which will work alongside the rest of your domain records.
RRSIG Record (RRSet Signature)
Record Resource (RR) sets are needed to secure a DNS zone. This is done by grouping records by type and name and making them into an RRset. Rather than validating each individual record, the RRset is signed. An RRSIG record stores the digital signature of an RRset for a domain using DNSSEC.
DS Record
A DS record instructs nameservers as to which key is next in the chain of trust and is what authenticates the relationship between a parent and child zone. This record includes a hash of the child zone’s DNSKEY. The hash is used to verify the public KSK. If the DS record from the parent zone matches up with the public KSK of the child zone, resolvers know they can also trust the rest of the child zone’s records.
DNSKEY Record
There are usually two DNSKEY records, one holding the public key for the ZSK and one holding the public KSK key. This record allows resolvers to verify a signature’s legitimacy.
How Can DNSSEC Help Secure My Domain?
One of the biggest advantages of using DNSSEC is that securing DNS lookups helps protect your business and your customers. Because DNS was designed with scalability in mind rather than security, it is vulnerable to certain types of attacks. The most notable threats are spoofing attacks, DNS or cache poisoning, man-in-the-middle, and hijacking attacks.
Of course, DNSSEC alone isn’t always enough to thwart cybercriminals. Services like DNS failover and real-time anomaly detection are vital to keeping your domain safe from distributed denial-of-service (DDoS) and similar attacks, —and they pair nicely with DNSSEC.
Who Needs DNSSEC?
DNSSEC can benefit any business, but it is especially beneficial for organizations that handle sensitive user information (both internally and externally).
While DNSSEC is an excellent security measure for DNS, it does have its caveats. For starters, it can create a compatibility nightmare. It’s also not supported by all registrars. Furthermore, it can be difficult to configure and implement correctly and typically comes with additional costs.
Despite the drawbacks, DNSSEC is a worthy addition to your domain’s security arsenal. Luckily, our DNS experts help you configure DNSSEC for your domain to ensure a seamless process via phone, support ticket, or live video chat.
It’s All About Trust
Like any good relationship, DNSSEC relies on trust—specifically, a chain of trust. And that is what the cryptographic signatures and keys are for. By having keys that authenticate each other, one public and one private, DNSSEC allows you to secure the DNS lookup process and provide higher security for your domain.
Related Resources:
